Web Application Threat Modeling
What is Web Application Threat Modelling?
Threat modelling is an approach for analysing the security of an application. It is a process by which potential threats can be identified, enumerated, and prioritised – all from a hypothetical attacker’s point of view. The purpose of web application threat modeling is to provide defenders with a systematic analysis of the probable attacker’s profile, the most likely attack vectors, and the assets most desired by an attacker. Application threat modeling answers the crucial questions like: “Where are the high-value assets?”, “Where am I most vulnerable to attack?”, “What are the most relevant threats?”, “Is there an attack vector that might go unnoticed?”.
Conceptually, most people incorporate some form of threat modeling into their daily lives and don’t even realise it. Commuters use threat modeling to consider what might go wrong during the morning drive to work and take preemptive action to avoid possible accidents. Children engage in threat modeling when determining the best path toward an intended goal while avoiding the playground bully. In a more formal sense, threat modeling has been used to prioritise military defensive preparations since antiquity.
Approach & Methodology
softScheck web application threat modeling will systematically identify and rate the threats that are most likely to affect your system. With threat modeling, softScheck is able to help you ensure that applications are being developed with security built-in from the very beginning.
Our web application threat modeling report will provide you with a greater understanding of your organisation’s system. It allows you to have better visibility of where the entry points to the applications are and the associated threats with each entry point.
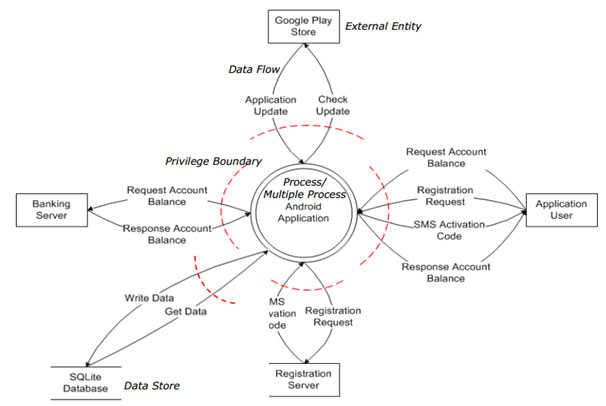
Secure Your System with softScheck
As a leading CREST accredited cybersecurity consultancy firm, our goal is to promote IT security from inception to completion for companies across a broad spectrum of specialisations. In addition to web application threat modeling, we are also experienced in other audit services like System Security Acceptance Test (SSAT), Information System Audit and Compliances, and Access Control Review, among others. We are also a trusted partner for security testing and advisory services. Get in touch with us to find out about our cybersecurity services today.