Ways to prevent Supply Chain Attacks to happen

In late 2020, an incredible story broke: US government agencies, including Commerce, Treasury, and Homeland Security, had been severely compromised through a malicious backdoor surreptitiously implanted into network management software supplied by a trusted vendor, SolarWinds. Weeks later, tens of thousands of organizations were scrambling to deploy a set of emergencies “zero-day” patches for Microsoft Exchange Server in an attempt to prevent another series of catastrophic compromises. As incredible as those events have been, supply chain attacks are neither new nor surprising.
Despite the subtlety involved in this attack, it is still possible to prevent a supply chain attack. Under the guidance, principles of supply chain security are divided into several stages.
Understanding your supplier security posture and the potential risks – Before engaging your supply chain/vendor, ensure you know their security posture and the potential risks that may posed by your supply chain.
Communicate the security standard that you have to your supplier and ensure to regularly assess their security posture such as through 3 rd party risk assessment.
Raise security awareness and support your suppliers in security incidents, technical baselines, and building security into contractual processes.
Build assurance process to manage suppliers and supply chain security at scale.
Encourage ongoing improvements and maintenance of trust with suppliers.
To fight supply chain attacks, companies can integrate a number of techniques, ranging from addressing issues with their general cybersecurity infrastructure to ensuring endpoints are secured against infiltration.
1. Staff Eduction
People are the primary target for cybercrimes because they are usually tricked into permitting cybercriminals access into an ecosystem.
The most common form of trickery is scam emails (or phishing attacks). These emails seem like they’re sent from trustworthy colleagues but upon interacting with them, the malicious code planted on the email will be executed that could lead to internal system access. This access is then further abused by the attacker to hunt for higher privileged accounts.
To prevent such incidents, all staff (yours and vendor’s that has access to your system) need to be educated about common cyberattack methods so that they can identify and report breach attempts, rather than falling victim to them.
2. Detect vendor data leaks
Data leaks are unintentional disclosures of sensitive data. If these leaks remain unremediated, they could be exploited by cybercriminals and used to launch supply chain attacks.
Many vendors are unaware of their own data leaks and leave them exposed. By implemented a third-party data leak detection solution, vendor data leaks can be detected and remediated before they have a chance to develop into supply chain attacks.
3. Implement a Zero Trust Architecture (ZTA)
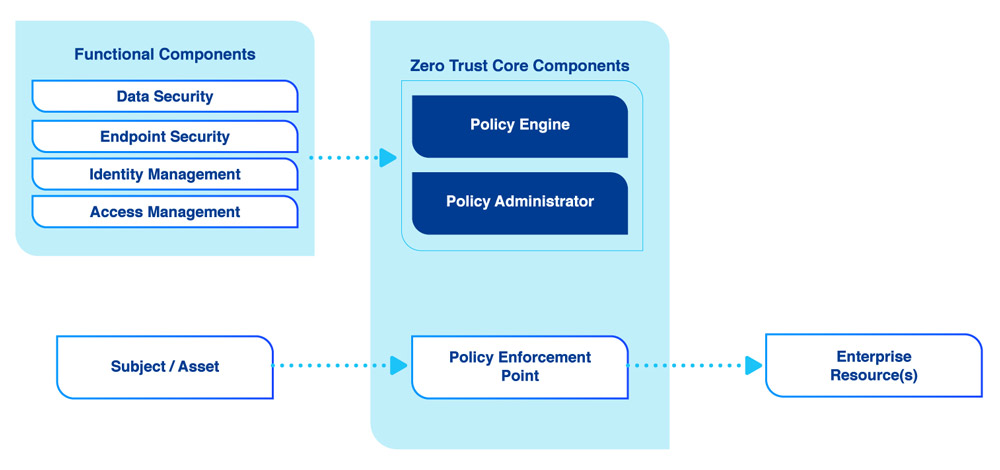
A Zero Trust Architecture assumes all network activity is malicious by default. Only after each connection request passes a strict list of policies is it permitted to access intellectual property.
At a high level, a ZTA is powered by a Policy Engine (PE), a Policy Administrator (PA), and a Policy Enforcement Point (PEP).
The Policy Engine decides whether network traffic should be permitted by following the rules set by the Trust Algorithm. The Policy Administrator communicates the Policy Engine’s decision (pass or fail) to the Policy Enforcement Point.
The Policy Enforcement Point is the final gatekeeper that either blocks or permits network requests based on the Policy Engine’s decision.
4. Implement strict rules for shadow IT devices
Shadow IT refers to all IT devices that are not approved by an organization’s security team. The recent global adoption of a remote-working model has resulted in many employees incorporating their own private IT devices while establishing their home office environments.
IT security departments should enforce the registration of all IT devices alongside strict guidelines about what can and cannot be connected. All permitted devices (especially IoT devices) should be monitored to identity DDoS attacks being launched from the supply chain.
5. Reduce the Risk from Developer Endpoints
Many supply chain attacks focus on compromising developer workstations or development environments. A developer workstation, which has permission to commit code to the CI/CD pipeline, is a “jackpot” for attackers. This is how the infamous SolarWinds attack breached the company’s build pipeline and was able to deploy malicious artifacts directly into its product.
You should comprehensively protect any endpoint – workstation, server, or cloud virtual machine – that is part of your organization’s build process. This can be done by deploying endpoint protection platforms, including endpoint detection and response (EDR) technology, which can detect anomalous behavior on endpoints and facilitate immediate response by security teams.
6. Implement an Identity Access Management (IAM)
With an IAM, multiple access privileged accounts can be managed from a single interface. This will ensure all privileged accesses are accounted for, preventing exposure risks from dormant accounts.
7. Encrypt all internal data
Data at rest and data in transit should be encrypted even though its internal data as the internal network are as vulnerable as the external network and the threats can comes both from internal and external. Encrypting internal data also provide additional layer of defense and supporting the ZTA policy.
8. Test your backup plan
The day disaster strikes is not the time to find out if your disaster recovery plan is well designed. Instead, simulate a worst-case scenario ahead of time and see if any gaps emerge.

Ongoing validation of your processes and controls is a must. Without it, you won’t know your blind spots and where improvements are needed. Get in touch to discuss your security concerns – we do not endorse any products. You will receive a true third party opinion based on your environment, sector-specific context and guidelines.

About softScheck
softScheck is an experienced cyber security consultancy firm that can help you with the prevention of Dependency Confusion through our service offerings. We perform IT Security Audits to inspect how your company manages your repositories and your policies on the retrieval or use of public packages, with the aim of compliance with security best practices. We also provide Web Penetration Tests to ensure your list of internal libraries and packages are not publicly exposed and provide recommendations to reduce any unnecessary exposure.
Please contact our friendly BD Director at [email protected] for a more in-depth discussion on how we can help your organization mitigate against Dependency Confusion and improve your security posture.



